
Azure
Microsoft Azure is a cloud platform for developing and deploying applications, data, and compute resources, as well as for running Microsoft applications globally. Azure AD provides the access management framework for all users, resources, and systems running on the platform. Azure AD is similar to Microsoft Active Directory (AD), but doesn’t use hierarchical naming structure or the protocol found in the Lightweight Directory Access Protocol (LDAP) standard. Instead, Azure offers a flat name space for all user accounts and uses groups and roles to manage user access to resources. Also, Azure AD provides Service Accounts for non-human users, such as applications.
Overview
The Trustle connector for Microsoft Azure provides both the ability to manage access to Azure cloud resources and manage Azure AD resources such as users, groups, roles, and service accounts. System owners and provisioners can view the dashboard, which provides an overall health check of your Azure platform in the form of a “Trustle Score,” as well as a full list of accounts on Azure, their exposure to risks, and recommendations on how to remediate or avoid such risks.
System owners and provisioners also can see a full list of resources available on the Azure instance and specify which of these should appear (and therefore be requestable) by users. Trustle provides defaults, but these admins can also specify the sensitivity of Azure resources, which alters the approval routing workflows and context queues accordingly.

Identity Management in Azure
Microsoft recommends managing access to Azure resources through its Role Based Access Control (RBAC) feature and through group membership; in fact, Microsoft documentation reads, “When you plan your access control strategy, grant users the least privilege required to get their work done.” Enabling this principle of least privilege requires familiarity with the platform, sensitivity of the services offered, and the ability to monitor and remediate changes that can take your Azure instance out of policy.
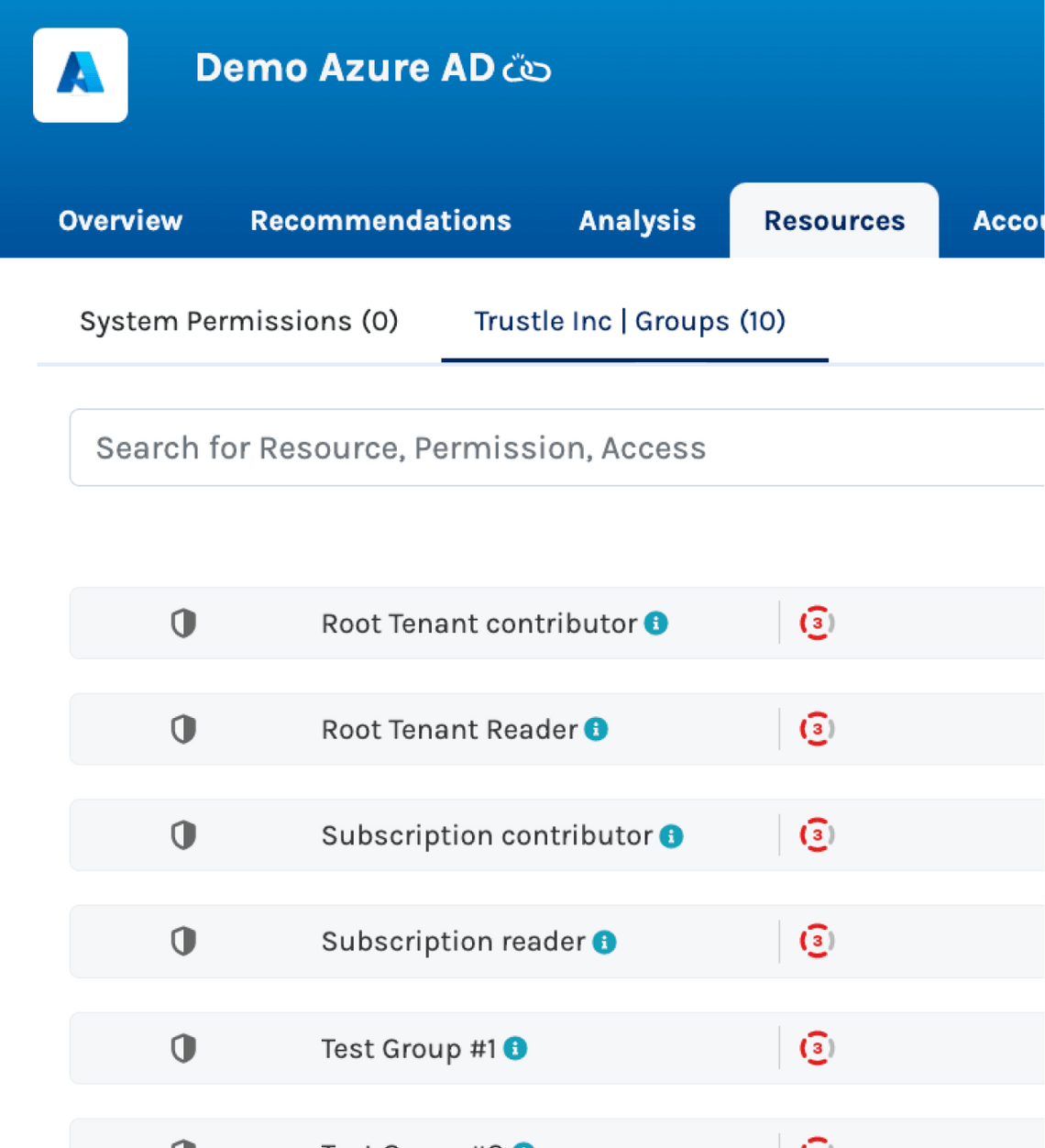
For example, Azure has several defined roles, such as Owner and Contributor, which should be reserved only for those users whose job it is to manage the Azure instance at that level. Other roles create much less exposure on the system. Azure also provides the ability for your organization to create custom roles–something the Trustle connector also picks up on and manages—but the additional roles can make administration more difficult. And of course, in non-production environments, it may be acceptable for non-ops personnel to have be an Owner, but this can become complicated to manage as the number of Azure environments grows in your organization.
Trustle enables system owners of all environments—whether Test, Dev, Prod, or otherwise—to manage their permissions and instances in a distributed, yet coordinated manner. This enables deployment pipelines to be continuously secure and monitored, while keeping administration overhead low for any given person.
Baseline Management of Accounts
Microsoft identity management has long distinguished between human users and service accounts, and Azure continues in this tradition. In addition, Azure provides robust RBAC features that Trustle helps you harness.
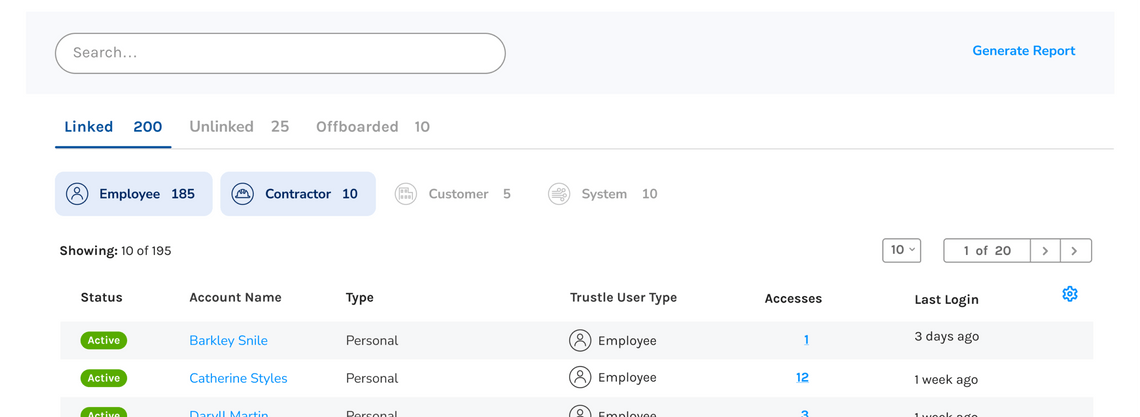
Trustle discovers all the users on Azure, as well as profile data for those accounts. This helps you link accounts to Trustle users and manage access with precision.
Trustle detects system accounts on Azure and helps manage their access and visibility.
Trustle discovers all roles—including custom roles—and enables you to manage membership in those roles.
Operationalize Azure Security
Microsoft provides many frameworks for managing access to cloud resources, but this essentially adds up to good advice—the real work is left to the customer to implement. This is where Trustle comes in: Trustle helps you organize and operationalize good security practices. Trustle helps you right-size the access of your service accounts and enables you to move infrequently used resources to Temporary or Just-in-Time access. This means that users who need infrequent access to valuable assets and data can gain that access easily, while making their accounts less useful or attractive to attackers.
Questions? Send us a note!
If you are just looking to ask us a quick question, feel free to send us an email at:
[email protected]