The Vandelay Chronicles: Access Management for All
Volume 1: A day in the life of a principal engineer at a high growth tech company
Question: Who doesn’t love a pop quiz, especially when it concerns your enterprise’s data security?
Answer: Nobody doesn’t love a pop quiz concerning your enterprise’s data security! So let’s get right to it! Do you know, or can you find out within seconds:
- If your users possess by default zero standing access, least privileged access, full access, or some combination of one or all to your company’s resources?
- Who has access to what data at your company?
- What your internal standards and processes are for requesting [preferably just in time (JIT)] access requests from zero standing to least privilege?
- Your process / criteria for approving those access requests in a speedy manner to keep your workforce on-task, efficient, and productive?
- In the event of a security event or audit, do you have the paper trail needed to demonstrate you knew who had access to what, approved by whom, and for what duration?
If your answers are complicated, or if you struggle to answer them at all, you’re not alone. Here at Trustle, we help our customers answer these questions by providing them with better control over their least privileged data access request, auto-revocation, visibility, and audit processes.
To spotlight how Trustle can help your company address these issues, we proudly introduce to you The Vandelay Chronicles, a Trustle blog series dedicated to examining “a day in the life” of employees who need least privileged access on-demand to specific resources to do their job, or are charged with reviewing, approving (or denying) access requests for teams they manage.
In our first edition of the series, let’s examine self-service, JIT elevation from Zero Standing to Least Privileged access in a Google Workspace / GitHub environment. Within this environment, we’ll demonstrate a user from Vandelay Industries requesting access at the ID provider-level (requests to the Google Workspace GitHub SAML app), as well as at the service provider level (requests to a specific team at the GitHub level.)
In these access request scenarios, what plays out in a world without Trustle, vs. a perfect world of access management bliss with Trustle? Keep reading to find out!
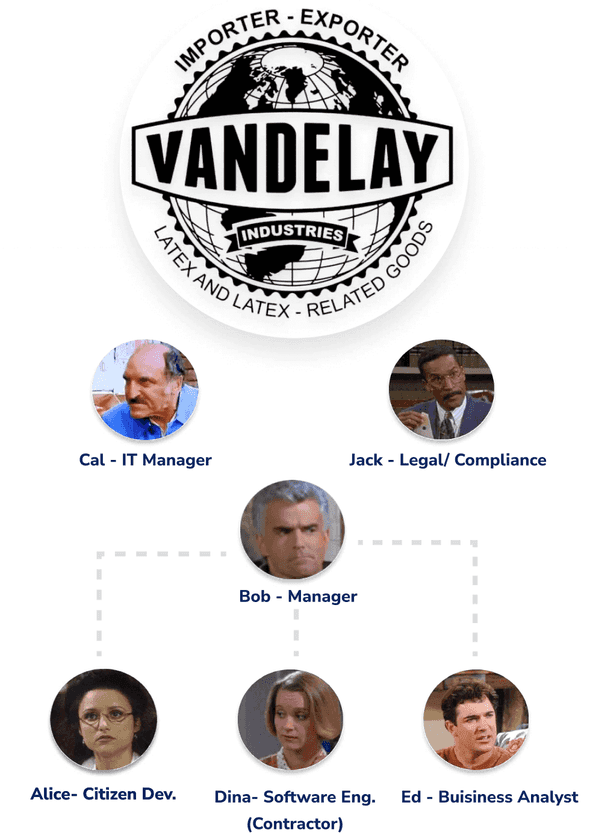
Get to know “Vandelay Industries”
Vandelay Industries is an early stage, remote-first, US-based Technology company with about 1,000 employees. The good news is they’ve experienced accelerated growth over the past year. The bad news is, given their fast pace of growth, requests for access to applications managed by their Google Workspace IDP have been increasing to the point their IT admins are nearly blindly approving requests in order to keep the request backlog at bay.
Vandelay Industries’ IT has historically managed the company’s access permissions through a spreadsheet. This may have gotten them by in the company’s more formative years, but is not scaling to match their recent growth. Their IT is now drowning in permission requests and slowly (if ever) revoking access. Now more than ever, with more business and more employees (which naturally brings with it a larger attack surface), they need a more efficient solution which will stand up to compliance requirements.
To give them credit, they began with no IDP at all; they discovered (and adopted) the benefits of a centralized user directory and SSO, adopted some tools and processes here and there to help manage risk.
Regardless, there are still blindspots between their IDP and third party tools which prevent them from having proper visibility into who has what, why, and who approved it. Not to mention, they are lacking a self-service system which manages access requests, access auto-revocation, risk and security posture scoring, and audit reporting.
Let’s take a look at how organizations like Vandelay used to operate with “coarse grain” access, and how Trustle can provide improved, “fine grained”, Just in Time (JIT) entitlements.
Life Before Trustle
Meet Alice, a Principal Engineer at Vandelay Industries. She has worked with the company since its inception, and remembers the good old days, when gaining access to customer data wasn’t such a hassle.
Today, with so many levels of management and departments being more closely monitored by the security team, she feels like her requests go into a black hole, and it’s frustrating to get her work done. Requests have gone from being granted in a few minutes, to taking days to weeks to get approved as the organization has grown.
A day in the life of Alice, Principal Engineer at Vandelay Industries
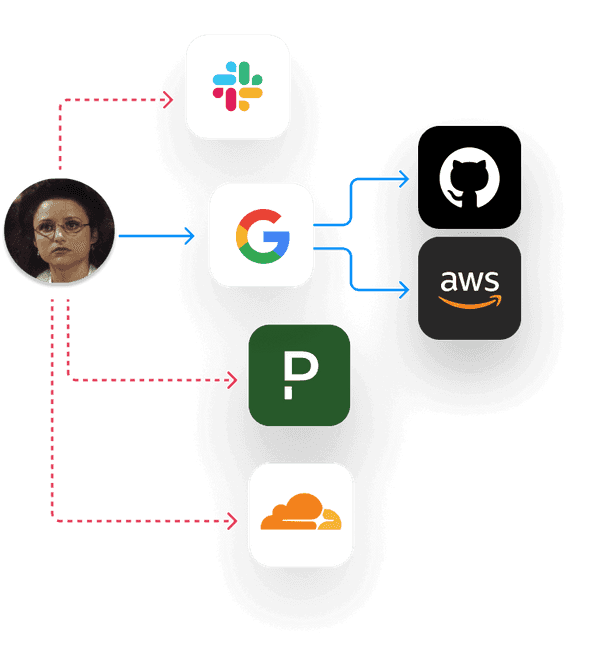
To troubleshoot customer issues, Alice first reviews logs and technical notes stored in Google Drive. If she can identify the issue via these logs and notes, her next move is to make and push code changes to associated GitHub repositories.
She always has access to Google Drive and can always read the logs and notes effortlessly. Having always provisioned access to Google Drive makes Alice very happy, because it's one less thing she needs to request access to. Cal, the IT Manager, and Jack in Compliance however know it's a liability, but given how backed up IT is with approval requests right now, they’re reluctant to add any additional controls.
Alice always has access to GitHub as well (much to the chagrin of Cal and Jack), but luckily (at least for IT and Compliance’s sake) she needs to request access to specific GitHub teams in order to gain access to their associated GitHub repositories.
In order to gain this access and complete her tasks, she creates an entry in a spreadsheet, and waits. Her requests are typically approved within a couple of days (hopefully), by some person she doesn’t work closely with, in some other state.
Using spreadsheets for this sort of thing is inconvenient, not to mention error prone, and lacks visibility for all stakeholders (including the requestor) of where in the process the request sits. Even if Vandelay Industries switches to a ticketing system for this process, it would still be going to an administrator who has no idea who Alice is, has never met Alice, and doesn’t know the customer; they are being asked to approve something very important that they have very little context around.
Alice understands the importance of security, especially as the company continues growing, but at the end of the day, she just wishes the process could be expedited. Why can’t she just work with her manager, Bob, to get the access she needs?
Luckily for Alice, she recently moved her at-home office to her in-law’s cabin on Lake Tahoe for the summer. While she waits for that administrator to approve her access requests, she enjoys the view of the lake and scrolls through Reddit. Sometimes with a coffee, sometimes not.
Eventually, Alice’s request is approved, and she can get back to supporting that customer (who at this point, may be feeling like Vandelay Industries isn’t taking their customer support request seriously, which is bad for business).
Sadly for Vandelay Industries, an audit is coming up, in which they will need to provide a ledger of access requests, approvals, and denials. As there is currently no record of Alice receiving this access, when it was granted, and why. When the audit commences, they will need to scramble to piece together the truth of who has access to what systems and why, across multiple systems and people, causing more chaos, headaches, and hair loss.
Life With Trustle
On a bright sunny day which will go down in history as the day Alice, Cal, and Jack became the happiest people on the planet, Vandelay Industries starts working with Trustle to implement intelligent, context-based access control.
Suddenly, Alice’s wish comes true - she can work directly with her manager, Bob, to gain access to the types of data and systems she needs to support her customers. But how?
Vandelay Industries continues to use Google Workspace to grant their users SSO access to GitHub, but with improved security, efficiency, and audit trails.
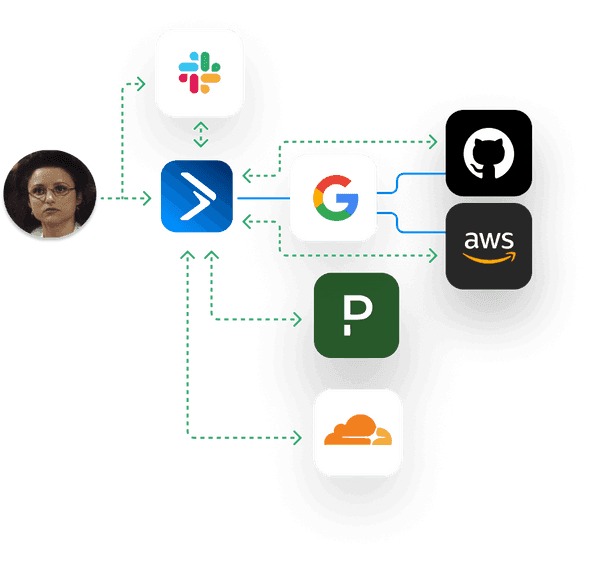
With the Trustle platform hustling in the background for Vandelay Industries, now Alice’s access and permissions requests no longer float off into the void.
Zero Standing Access to Google Drive until Least Privileged Access is Needed
Instead of Alice (and other employees) always having standing access to Google Apps (such as Google Drive), by default, they will have zero standing access, until it's needed.
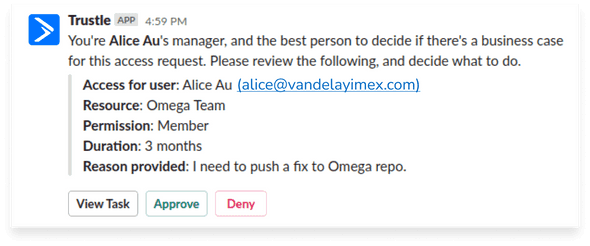
To access the logs and notes within Google Drive, Alice, via Slack, requests access to the Google Drive app itself. Bob gets the request immediately via Slack, and approves least privilege access for a predefined amount of time, so Alice can keep on her way. Once approved, Alice is notified via Slack and email, and she can proceed to triage the issue. Once she’s gathered the data she needs, she’s ready to pull the code and work on a fix.
Zero Standing Access to the GitHub SAML App and GitHub Teams until Least Privileged Access is Needed
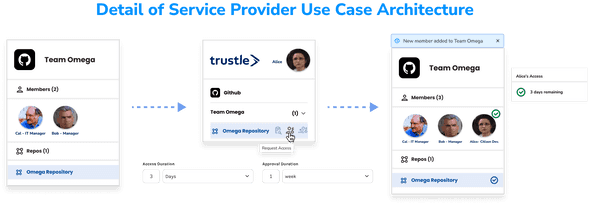
Alice next requests access to the GitHub [SAML] App, and the GitHub Team (associated with the GitHub repository) she needs to make and push her fixes. Just like before, via Slack she can request what she needs and why, and her manager can quickly approve from Slack to keep Alice productive.
Bob, who is intimately aware of Alice’s work and the customer needs, is alerted to the request within the company’s Slack. Bob can approve least privilege access, for a defined amount of time, directly through the Slack interface.
Upon Bob’s approval, Trustle calls GitHub APIs to move Alice into the requested GitHub Team, which is associated with the necessary repository access.
After a day, Trustle is configured to revoke Google app, GitHub App, and GitHub Team access automatically from Alice, resulting in a logged, return to zero standing access for Alice (and her virtual identity). Because Bob let Trustle know its ok to grant Alice JIT, least privileged access to those resources as she needs them for the next three months without his consent, Alice can quickly re-request and gain access to them instantly as new support requests roll in.
And get this… Trustle was able to increase resources kept at zero standing privilege (from one to three), while decreasing approval time for these three resources from days to seconds. The customer’s support request is addressed much faster than “Life Before Trustle”, because Alice’s need for access to Google Drive and GitHub can be verified, approved, and revoked in a more streamlined process.
Trustle’s easy-to-use access management solution helps Vandelay Industries:
- Account for, and verify ownership of, every account and resource in your organization.
- Enable just-in-time (JIT) self-service access to accounts and resources in your organization.
- Create access request workflows that provide delegated approval processes customized to the sensitivity of the accounts and resources being accessed.
- Provide reporting and visibility into who approved what access for someone, when, why and for how long.
- Verify properly scoped permissions based on Risk and Usage scores.
More About Trustle
Try Trustle today! Sign up for a free trial in just minutes. And don’t leave without checking out our blog for ongoing thought leadership and expert insights on identity and access management, cybersecurity and data security topics.