AWS
The IAM Service in AWS is the interface for managing all access to resources in the system. Amazon offers several different approaches for relating user accounts (both human and non-human) to resources on the platform. Usually, these are assigned by group, role, and policies, rather than direct access policies to AWS resources such as services, S3 buckets, or databases. Amazon provides an API to the IAM service, which enables third-party developers to orchestrate access to resources.
Amazon doesn’t offer native support for just-in-time or temporary access to resources on the platform, so it can become difficult to manage if your goal is to implement least privilege.
Overview
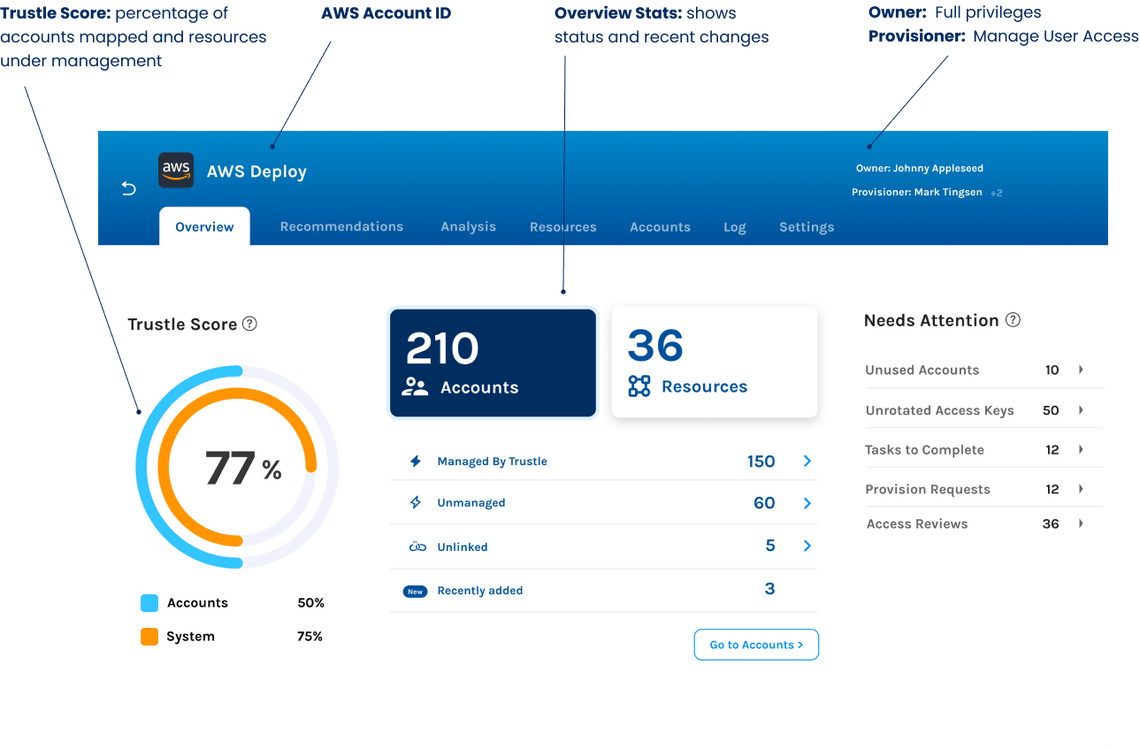
The Trustle AWS connector provides both deep visibility into AWS IAM and the ability to manage IAM resources. The connector can be deployed in a read-only or read/write mode, based on the AWS policy (a template policy is provided as part of the connector setup). You can also change this behavior through the Trustle connector settings. Once configured, the Trustle AWS connector continuously monitors AWS IAM and provides a full read-out on all accounts, privileges, and policies on the platform. Using this information, Trustle provides recommendations for adjusting system settings and IAM configurations.
The following image shows the Overview page for the AWS connector in Trustle.
Inspect all AWS resources
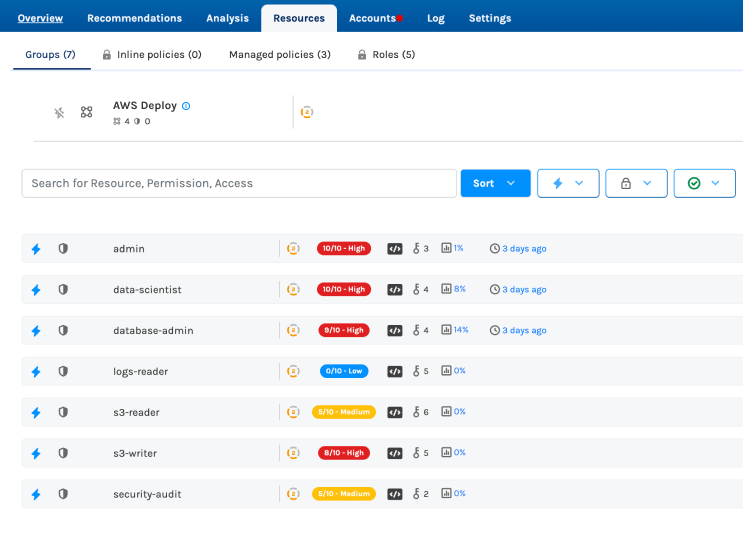
The Trustle AWS connector gathers a wide range of information from AWS to help you understand who has access to what, as well as how that access is used. Trustle gathers information about the following:
- All accounts on the platform (including human users and non-human / service accounts)
- All groups and membership in the groups
- All roles, who has access to roles, policies associated with roles, and usage
- All policies, including both managed and in-line policies, for resources on the system
- Services available and services accessible by each user
- Usage data for each user
Resources the AWS Connector Inspects
The AWS connector gathers a substantial amount of information from IAM, including usage data, that provides a detailed high-level view of how AWS is configured.
Because many accounts on AWS are used by “non-human” actors, many of the user accounts won’t appear in a corporate directory or identity provider. However, all accounts are discovered and represented in Trustle.
AWS doesn’t enforce token rotation, but Trustle can alert you to tokens that have passed their stated expiry and that should be rotated.
Trustle is able to monitor usage patterns for user accounts, groups, and roles and can recommend what level of access is actually needed. You can use Trustle to right-size privileges for each user, while allowing users to easily gain greater access as needed.
Manage access to AWS resources
With Provisioning enabled and with the Write policy active on AWS, the Trustle connector can automate changes to IAM. For example, when a user requests access to a resource and a manager approves, Trustle can automatically add the user’s account to the associated resources. This makes just-in-time access on AWS easy, manageable, and secure. Trustle maintains a history of all access requests, all workflows, and all changes to the system, so your security team and auditors can discover any evidence needed to show compliance.
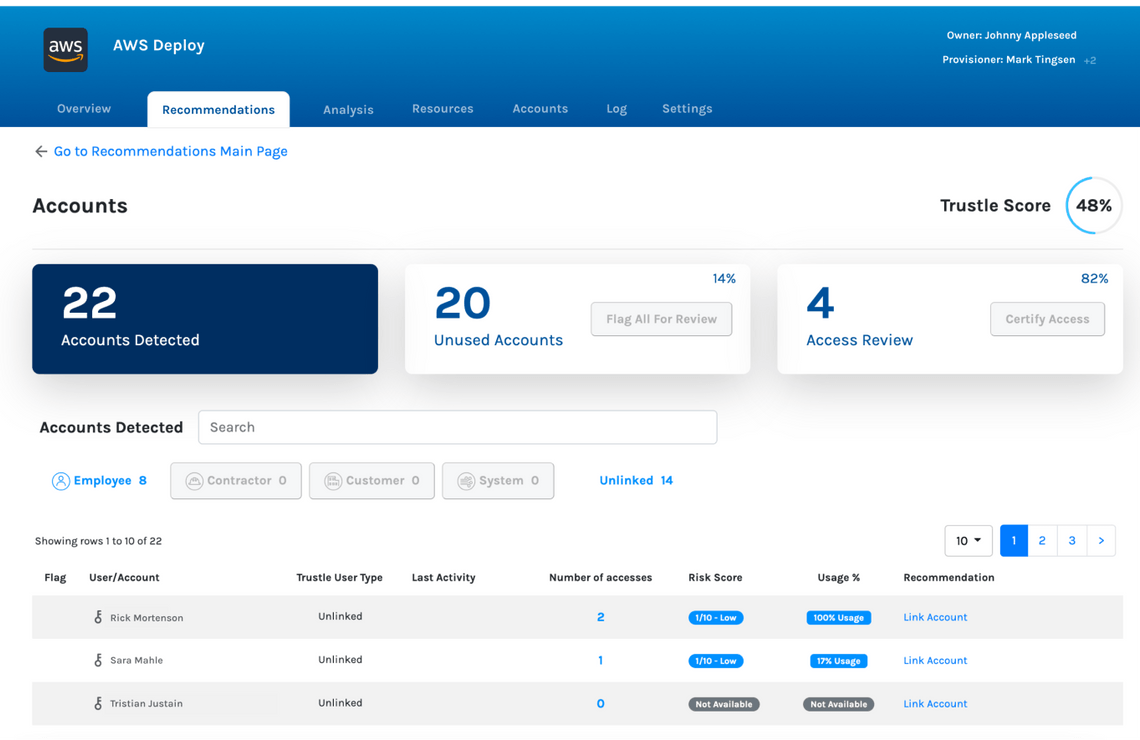
With the information gathered from AWS and through usage data, Trustle makes recommendations for improving the security posture of the platform. For example, Trustle will recommend removing access from user accounts where the access is not needed (least privilege), removing user accounts that are no longer in use (account cleanup), and increasing the sensitivity rating on high risk resources. Trustle also recommends rotating tokens at set intervals and when to review specific accounts.
Additionally, Trustle highlights accounts with Access keys and Certificates that need rotation and accounts that need multi-factor authentication (MFA) enabled. Based on metrics of the sensitivity of the resource or service, compared with the amount of usage the account requires, Trustle also identifies opportunities to move these entitlements to Temporary or Just-in-Time, ensuring that access to these resources are guarded by “least privilege” principles.
Questions? Send us a note!
If you are just looking to ask us a quick question, feel free to send us an email at:
[email protected]